By Jonah Berg-Ganzarain
A pair of doctoral students and their advisor, looking for insights into the inner workings of tech support scams, spent eight months collecting data on and studying the tactics and infrastructure of the scammers, using a purpose-built tool. What they uncovered is a complex, technically sophisticated ecosystem supported by malvertising and victimizing people around the world.
The study is the first analysis of its kind on tech support scams, and it’s the work of two PhD candidates at Stony Brook University, and their advisor, Nick Nikiforakis. The team built a custom tool called RoboVic that performed a “systematic analysis of technical support scam pages: identified their techniques, abused infrastructure, and campaigns”. The tool includes a man-in-the-middle proxy that catalogs requests and responses and also will click on pop-up ads, which are key to many tech-support scams.
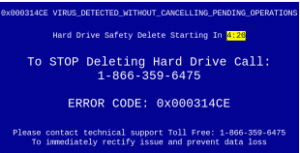
There are a slew of different versions of these scams, but generally they’re a type of multichannel fraud that occurs when a scammer claims to offer legitimate tech support via the phone or online to unsuspecting users, with the caller usually claiming to work for Microsoft or Apple support. As the Stony Brook study points out, many of these scams begin when a cleverly designed website tricks unsuspecting, vulnerable users into believing they have a virus, and that they need to call the number shown on the site to help them out. Sometimes, the page disguises itself as a Windows “blue screen” so that users find it more believable.
In their study, the researchers found that the source for many of these scams were “malvertisements”, advertisements on legitimate websites, particularly using ad-based URL shorteners, that advertised for malicious scams. This gives the scammers an opportunity to strike on what would seem like a relatively safe page. Although victims of these scams can be anywhere, the researchers found that 85.4 percentof the IP addresses in these scams were located across different regions of India, with 9.7 percentlocated in the United States and 4.9 percent in Costa Rica. Scammers typically asked users for an average of $291, with prices ranging from $70 to $1,000.
“This threat is not going to decrease soon.”
“Technical support scam is a multi channel scam that benefits from both the telephony channel and web channel to spread and perform the attack and it makes it difficult to track it and take it down.” said study co-author Najmeh Miramirkhani, a PhD Computer Science student at Stony Brook.
The researchers used RoboVic to collect data over the course of the eight-month study, and then called 60 scammers, posing as naive users, and gathering information on the scammers’ social engineering techniques and demeanor. They saw a wide range of tactics and concluded that while there may be a few individual scammers operating, the vast majority of them are part of large, organized call centers. Many of the scammers also use technical tools to help run their fraudulent operations.
“We discovered that scammers abuse popular remote administration tools (81% of scammers rely on two specific software products), to gain access to user machines where they then patiently attempt to convince users that they are infected with malware. We found that, on average, a scammer takes 17 minutes, using multiple social engineering techniques mostly based on misrepresenting OS messages, to convince users of their infections and then proceeds to request an average of $290.9 for repairing the ‘infected’ machines,” the authors said in their paper.
This sort of scam is showing no signs of decline, Miramirhani says.
“So far, we collected more than 25K scam domains and thousands of scam phone numbers and we [have] evidence that this threat is not going to decrease soon and it still has an increasing trend,” Miramirhani said.
The authors stress that it’s important to educate individuals on how to avoid these types of scams, and suggest measures such as a browser extension that warns users about scam sites or a general education program. While older people and individuals unfamiliar with technology are the most vulnerable, the most important thing to do for everyone is to engage them in training to learn when to spot this multichannel scam.
The FTC has been cracking down on these scams for several years, and just this week shut down an operation in which the alleged scammer was pretending to represent the FTC itself while offering fake tech support.
Image: Greyweed, CC By license.