Call Center Fraud: The Playbook For A Strong Defense
As government relief programs began to taper off and the availability of government funds decreased, Pindrop observed fraudulent activities beginning to shift back towards financial institutions.
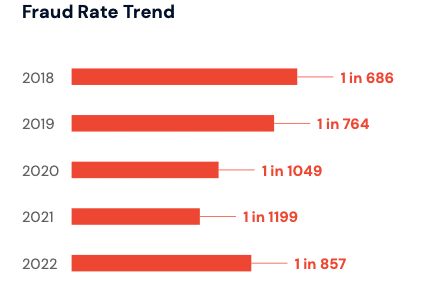
According to Pindrop’s intelligence, the trend of declining fraudulent activity within our client base began in early Q2 2020 and lasted through all of 2021. However, things began to change in 2022. The first quarter in 2022 saw a 35% increase in fraud attacks compared with the last quarter in 2021 and by the end of 2022, 1 in 857 calls analyzed by Pindrop were identified as fraudulent. This represents a 40% increase in fraudulent activity compared with 2021. This rapid increase to pre-pandemic norms should alarm any financial institution without strong safeguards in place.
Fraud in the contact center can be damaging due to vulnerabilities associated with knowledge based authentication questions, one time passcodes (OTP) and customer service representatives (CSR’s) ability to detect bad actors. What is particularly damaging is when fraud controls successfully detect/restrict unusual activity only for the fraudster to call in to the contact center and have those restrictions removed by a CSR.
Within this study, we will share with you common tactics observed along with a comprehensive approach to protect your call center and most importantly, the financial assets you manage to minimize fraud losses.
Fraudster Behavior: Understanding The Pattern
Before we go any further, it’s important to understand what it is that fraudsters are hoping to achieve when they impersonate your legitimate customers. Common examples of what the fraudsters wish to achieve include but are not limited to:
- Validation of SSN’s to moderate/high value account
- Monitor Account Balances
- Change contact information to those they control (phone number, mailing address, email address)
- Request a debit/credit card
- Reset online credentials (username / password)
- Remove fraud restrictions
- Gain approval on a transaction or money transfer that was declined/referred
The last two bullets are the most insidious. You could have the best controls in place to detect suspicious activity and restrict money movement but if the fraudster is able to convince your CSR that they are the genuine customer, all of that effort may be lost.
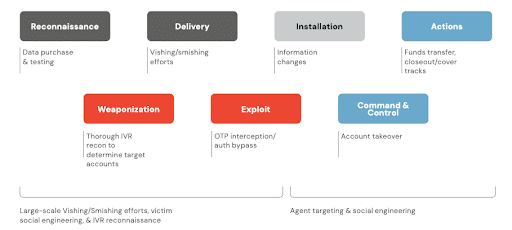
It’s also important to recognize that very likely, the fraudsters in question will make multiple calls accessing the target account. This activity typically originates in the IVR after PII has been successfully collected. Fraudsters will use IVR systems to conduct reconnaissance to validate the PII they have acquired matches to an account holder at the target institution along with monitoring the balances of the target accounts. This activity may escalate to the fraudster vishing the legitimate account holder, impersonating a CSR from the target institution, to collect answers to challenging KBA questions such as a verbal password or to have the legitimate account holder provide an OTP.
According to Pindrop’s intelligence, once an account is targeted by fraudsters in a phishing or account takeover attack, the likelihood of a secondary fraud call targeting that account within 60 days is between 33% and 50%. Even after 60 days have passed from the initial attack, the risk of fraud for a previously targeted account remains extremely elevated between 6% and 9%.
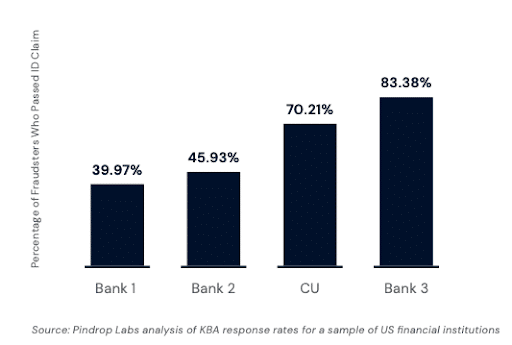
We also find that in most instances fraudsters are quite successful in passing the verification process when speaking with an agent. In analyzing our client data, we have found that fraudsters are able to pass agent verification 40% to 60% of the time.
Now that we understand what fraudsters are doing, let’s talk about how you can better protect your assets.
Applying A Comprehensive Defense Strategy
Leveraging Pindrop’s intelligence can help organizations by providing a more comprehensive understanding of potential threats in the call center, improve real-time risk assessments and decisions, and allow for more effective cross channel risk mitigation strategies. This is due to Pindrop’s core technology platform that assesses multiple factors when determining risk such as:
- Device audio characteristics
- Language independent voice characteristics
- Pattern recognition
- Carrier data and signaling
- PIN (consortium data)
Risk-Based IVR Call Routing
According to Pindrop’s intelligence, within IVR contained traffic, 1 in 390 accounts accessed is targeted by fraudsters and that the majority of these accounts have a fraud claim between 30 and 60 days of the initial fraud call.
Active prevention in IVR security uses risk-based intelligence to stop potential fraud during IVR calls. Real-time internal automation and filtering are used to identify “at-risk” accounts and modify the IVR call flow to limit functionality and access to account-specific data. This reduces the use of the IVR for reconnaissance and minimizes the negative impact on legitimate callers.
This method could be implemented by requiring additional verification during the IVR leg of the call to verify the identity of a caller and prevent unauthorized access to sensitive information. Active prevention is an important component of IVR security and can help to protect both the organization and its customers from potential attacks.
Risk-Based CSR Verification
It’s important to recognize that while CSR training is important, it is not, in itself, protection. We started off this study by highlighting that in 2022, 1 in 857 calls analyzed by Pindrop was identified as fraudulent. If the average CSR handles 50 calls per day, they would speak to one fraudster every 17 days. Risk awareness and training must be balanced with efficiency and positive customer experiences.
This means that automation and tools are best positioned to identify risky callers while limiting negative experiences to genuine customers. One such method recommended is consuming Pindrop intelligence in real-time via cloud based API’s. This intelligence can then be interpreted and used to influence visual prompts that are situated within the screen pop or agent desktop screen. This method ensures that each caller receives the appropriate level of verification while allowing the agent to focus on assisting the caller and ensuring a positive customer experience.
Post Call Fraud Cleanup
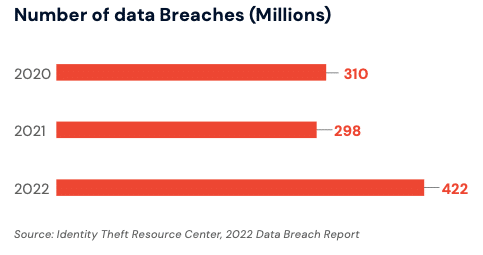
Even with risk-based call routing & verification, fraudsters will still find ways to get through the first lines of defense. This is due to the sheer number of data compromises occurring each year coupled with commonly used social engineering tactics by fraudsters. Since 2020, an average of 300 million victims have been affected by data breaches which shows how widespread and damaging data compromises are.
That is why it is important to have experienced fraud fighters reviewing the riskiest calls to ensure that if fraud occurred, steps are taken to mitigate any potential loss. This includes restricting online access to the account and restricting the ability to transact (card, check, wire, ACH & P2P) until the genuine customer can be reached and a fraud claim can be processed.
Mark, Monitor & Prevent
Lastly, one of the biggest mistakes organizations can make is assuming fraudsters are only attacking a single channel or only making a single call. Oftentimes, fraudsters will attack multiple channels at once and repeatedly. That is why it is important to leverage Pindrop’s intelligence within your other fraud controls.
Through Pinrop’s research we have identified that ~30% of fraudulent events take place within the first 30 days after an account has been targeted in the phone channel. However, ~70% of fraudulent events take place after 30 days with the majority failing within the window of 30 -60 days.
If it has been identified that an account is under attack from fraud in the phone channel, that intelligence should be leveraged to complement your other controls, especially controls that monitor credit card/debit card transactions and access to the digital channel as these are the most likely paths to monetization.
Conclusion
The process of implementing fraud controls in your call center may seem overwhelming at first but the value of doing so is significant. By deploying a comprehensive plan, you gain the benefits of:
- Protecting your customers data: with over 400 million data breaches reported in 2022, preventing fraudsters from using your IVR and/or call center agents to validate PII is crucial.
- Restricting the ease in call center initiated account takeover: 40-60% of fraudulent activity occurs with fraudsters able to pass KBA and/or OTP. Passive, multi-factor risk assessments reduce opportunities for human error and decrease the ability of fraudsters to have restrictions lifted and referred/declined transactions approved.
- Improving detection capabilities: integration of Pinrop intelligence to complement existing controls that monitor for fraud within the online channel and card space.
- Recognizing operational savings and customer experience improvements: reducing friction for your genuine customers through passive risk assessments.



