Researchers Release Master Decryption Tool for TeslaCrypt

The attackers behind the TeslaCrypt ransomware pulled up stakes and released the master decryption key for their creations, and now security researchers with Cisco’s TALOS team have published a tool that will decrypt files encrypted with any version of TeslaCrypt. The TeslaCrypt ransomware isn’t the most well-known or the nastiest of the variants that have […]
Canadian University Pays $15K in Ransomware Attack

A ransomware attack has cost a university in Canada more than $15,000, after the school’s network was compromised and brought to a near standstill. The University of Calgary said it was hit by the ransomware attack about 10 days ago and many portions of the college’s network were affected. The IT department has been working […]
Angler Exploit Kit EMET Bypass Leads to TeslaCrypt Ransomware

Microsoft has built a number of technical defenses against browser-based exploits in the last decade or so, including a specialized toolkit called EMET that’s designed to defeat advanced exploits. Attackers have now created a version of the notorious Angler exploit kit that can bypass EMET entirely and then install the nasty TeslaCrypt ransomware. This advance […]
Ransomware is Dope
Credit where credit is due: Ransomware is kind of brilliant. From a defender’s perspective, it is perhaps the most difficult threat to deal with in the last five or 10 years. It locks up your data, makes it inaccessible and unrecoverable (without backups), and presents you with, at most, two options: Don’t pay the ransom and […]
Life in the Ransomware Underweb
The business of ransomware is booming, and some of the criminals running these operations have so much work and money on their hands that they’re building out affiliate networks to help them handle it all. In their efforts to extort as many victims as possible with their malware, ransomware authors have been spreading their creations in […]
On the Wire Podcast: Ransomware

Ransomware is one of the nastier and more insidious threats to emerge in the last decade, and the attackers using it have targeted consumers and businesses alike. Threats such as CryptoLocker, Locky, Cryptowall, and many others have been locking up users’ files and demanding hundreds or thousands of dollars in order to decrypt them. Security […]
New Version of RansomWhere? OS X Detection Tool Released

The author of a generic detection tool for Mac OS X ransomware has updated the application, adding a number of new capabilities, including support for full file-system monitoring and support for older versions of the OS. RansomWhere? is a tool written by security researcher Patrick Wardle for the purpose of detecting and stopping ransomware behavior […]
Ransomware Attack and Defense
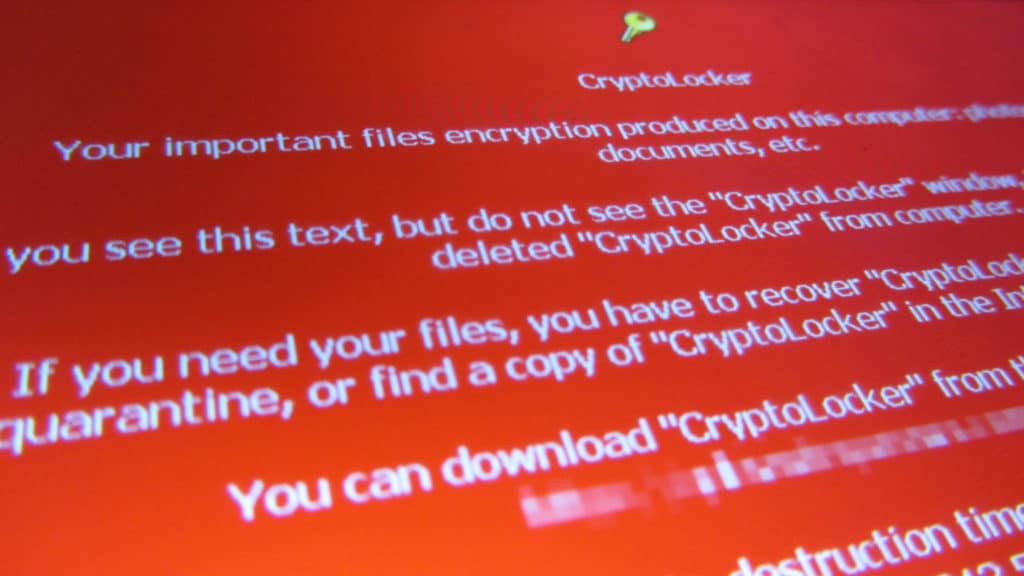
By Jessy Irwin In the US, ransomware is earning a significant amount of media attention for shutting down schools and hospitals, but a recent study points to Canada as the country 4th most likely to be a victim of ransomware attacks. With that in mind, this document presents background information, security recommendations and policy for […]
SamSam and the Rise of Corporate Ransomware

The SamSam ransomware that caused serious damage to a California hospital and has infected many other enterprises in the United States is continuing to evolve and add new functionality as its developers look to stay ahead of researchers and defenders. SamSam is part of the newer wave of ransomware variants that don’t just rely on individual […]