Articles
Anomaly Detection and Fraud Prevention Best Practices
Pindrop
author • 12th November 2020 (UPDATED ON 01/17/2025)
13 minute read time
Fraud costs don’t start in your finance department. They start in your IVR. 60% of fraud begins in or touches it and while you are aware of the media reported mega-breaches that have plagued companies and consumers both, have you considered your contact center’s place in the journey from data capture to fraudulent transaction and account takeover? Fraudsters stalk contact center IVRs using them as search engines for your CRM to validate customer data. They then use that validated customer data to social engineer your agents or commit fraud across other channels. Pindrop is turning the tables on fraudsters by creating a playbook to stop them.
If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.
― Sun Tzu, The Art of War
To help support contact center leaders in the arms race for customer data, Pindrop has assembled a curated collection of assets, research, and tools to help you bolster your defenses.
You can explore the tool kit on this page linearly or choose the section you need:
What is Contact Center Fraud?
Who Are The Victims of Contact Center Fraud?
Who Are The Victims of Contact Center Fraud: Your Customers
How Contact Center Fraud Impacts Elders and The Disabled
How Contact Center Fraud Impacts Children and Families
Who Are The Victims of Contact Center Fraud: Employees
How Contact Center Fraud Impacts: The Fraud Team
How Contact Center Fraud Impacts: The CX Team
How Contact Center Fraud Impacts: The Leadership
Who Are The Victims of Contact Center Fraud: Your Business
What Kinds of Fraud Targets Contact Centers?
Account Takeover Is The Goal
Social Engineering in Contact Centers
Call Spoofing in Contact Centers
Man in the Middle, The Customer Assisted-Attack
Fraud Tactics – Evolving in a contactless society
Where Do Attacks Begin in Contact Centers?
What is Contact Center Fraud?
Fraudulent activities like fake transactions and false information updates or activities supporting the eventual takeover of an account like data reconnaissance or social engineering – are all types of contact center fraud. Contact center fraud, therefore, is any fraud related activity occurring in or originating from the contact center – or more simply, your company’s phone channel.
Unsurprisingly, seismic changes in the way we interact with customers and the way they interact with us and each other have impacted call volumes and have exacerbated other operational challenges – opening the door for rising contact center fraud.
Who Are The Victims of Contact Center Fraud?
The victims of contact center fraud are often considered to be the customer themselves and of course the business. With common costs including chargebacks and other remediation efforts like card re-issuance fees; in addition to the actual monetary loss. But these are only a fraction of the victims and impacts of contact center fraud.
We discuss the real victims of contact center fraud below:
Who Are The Victims of Contact Center Fraud: Your Customers
Your customers come to mind as the first and most obvious victims of contact center fraud. Fraudsters are scraping your ivr to validate their information for nefarious use after-all, but what about their dependents, friends and family, and your most at-risk customers?
How Contact Center Fraud Impacts Elders and The Disabled
Elder fraud is heinous and unfortunately, it is increasing. The seniors that patronize your business are being targeted through information harvesting schemes online and via the phone channel. These phishing scams result in fraud reconnaissance activities in your IVR to validate the data and hone processes for account takeover. Contact center fraud specifically impacts elders due to their incapability of remediation.
How Contact Center Fraud Impacts Children and Families
Not often viewed as a casualty in the fraud fight, the identity of children, both of account owners and those that are actual clients is specifically at risk. Like the elderly, the credit histories of children are rarely monitored and as such are easy targets for cybercriminals and professional fraudsters. Uniquely the threat to children often includes the usage of leaked or stolen lifetime data like social security numbers, the compromise of which can cause identity on-going complications.
Who Are The Victims of Contact Center Fraud: Employees
How Contact Center Fraud Impacts: The Fraud Team
A fraud team’s capacity is often regarded as an obvious result of increased contact center fraud activity – but the costs concerning operations like time lost on false positives, complex fraud ring investigations, and increased fraud activity causes backlogs that put stress on what may be an already understaffed fraud team.
How Contact Center Fraud Impacts: The CX Team
Costs associated with churn like recruiting and training spends can be the result of anti-fraud systems that provide no support for your frontline, requiring investigations and inferences on the part of the agent.
Who Are The Victims of Contact Center Fraud: Your Business
Operations Costs
Operations costs associated with finding and fighting fraud are often over-looked. Costs associated with decreased analyst capacity but increased fraud can devour entire week’s worth of man-hours for an entire team, wasted on the remediation of one account takeover.
If your business is targeted by an organized crime ring, there could be as many as 10 professional fraudsters working simultaneously to defraud one organization. In this scenario, as many as 100 accounts would be controlled by fraudsters, resulting in 1600 hours of remediation.
16 Hours Per Compromised Account x 100 Compromised Accounts = 1600 Work Hours To Remediate
1600 hours of remediation is 40 analysts worth of work for an entire week. A week’s worth of wasted costs and productivity causes backlog and can result in more fraud losses and related remediation costs, ranging from several thousand per account, higher if the fraudster had been targeting the institution with reconnaissance activities.
Brand and Reputation Costs
1 in 3 consumers will abandon a brand after a negative experience like ATO, and over 90% will abandon their chosen retailer after 3 bad experiences. As we have necessarily shifted to a contactless economy- the phone channel is replacing face-to-face customer service and consumers overwhelmingly want to keep human interaction as an element when resolving an issue or otherwise interacting with corporations and organizations.
Your IT Security
A spike in fraud attacks may mean a network intrusion, exposed servers, or a third party breach. Additionally, leaky IVRs may allow for the validation of employee data that can be used for network intrusion and unauthorized access. The threat of contact center fraud effectively expands your attack surface as IVRs and the voice channel as a whole increasingly becomes a vector of choice in the contactless era.
Additionally, as dark web data finds itself into the contact center, should your employees use the same passwords across their personal accounts and your network, data validation in the IVR could potentially open new challenges that don’t target the consumer and instead focus on your company’s internal data.
What Kinds of Fraud Targets Contact Centers?
Fraudsters don’t rely on luck; they do their homework. They use multiple sources like purchased data, harvested from corporate breaches, and sold on the dark web and leaked data scraped from servers and unsecured pages to develop profiles on the organizations they target. They study how contact centers operate, the relevant policies for their endeavors, and have access to petabytes of personal data on their customers like name, DOBs, SSN, drivers license numbers, and more. They come prepared to answer security questions and have practiced strategies to bypass your security, authenticate into account, and get out before anyone notices.
Account Takeover Is The Goal
The goal of contact center fraud is account takeover. Account takeover allows for additional low-risk reconnaissance and the creation of additional synthetic identities. To accomplish this, fraudsters leave the dark web armed with “fresh data” and use it to target your contact center in a variety of ways.
Social Engineering in Contact Centers
Professional fraudsters understand human psychology, it is a part of their jobs. In the contact center when they interact with your agents they use this psychology knowledge along with distraction, empathy, trust-building, vishing, and basically harassing the agent into allowing access to the account.
Call Spoofing in Contact Centers
ANI spoofing allows bad actors to imitate a customer number to bypass IVR controls. Automatic Number Identification spoofing is a deliberate action that allows access to your frontline agents and enables social engineering.
Account Reconnaissance in Contact Center IVRs
Before ever attempting interaction with an agent, bad actors validate consumer information in the IVR. 60% of fraud originates in our at some point touches the IVR.
Man in the Middle, The Customer Assisted-Attack
Assisted by ANI Spoofing to the customer instead of your call center initially, consumers are duped into believing that they are interacting with a genuine agent as the fraudster literally plays the middle man live – calling into the bank with the customers spoofed number and giving your agent the correct answers directly from your customer.
Dark Web Data & Contact Center Fraud
Cross-channel fraud can be assisted by unidentified breaches or leaks which provide data for sellers and buyers on the dark web. Fresh and often guaranteed to be verified – bad actors simply bypass controls using a mix of spoofing technology and perfectly genuine data.
Fraud Tactics – Evolving in a contactless society
In early March, governments across the world began warning consumers of a sudden uptick in scams most likely driven by current and assumed-future conditions. Phishing scams that would evolve into fraudulent activity across banking, financial services, insurance, and other verticals. The fraudsters would adapt their social engineering appeals to reflect current events and play on anxieties too. Taking many standard techniques and simply adding a dose of the newsfeed.
Social Engineering Tactics – Changes Since The Contactless Shift
The Urgent Request
The Fraudster calls and says all my other banks are closing and I won’t have access to any money so we need to transfer money asap. They will make it sound like an urgent request, “we can’t wait” in hopes your agents will skip some steps to make the transfer happen.
The Philanthrope: The Fraudster calls pretending to be a client and says they need to access money quickly so they can donate to various COVID-19 related cures, treatments, clinical drugs, etc., and need to make a transfer to another account. Always rushing agents on the phone to act quickly.
International Traveler: The Fraudster calls telling the agent that they are stuck outside of the U.S. and need money ASAP so they can get back in. Again, playing on all the hysteria of being stranded overseas, away from family, to make it sound hectic and dire.
Elder Abuse: The Fraudster calls organizations pretending to be the caregiver of an elderly person who has become ill and needs help. These con-artists then phish for information on the actual client while on the phone with your agents. Then, they empty the elderly person’s account, or they call in again to see if they can phish for more information.
Traditional Phishing: Fraudsters using social engineering to garner information from your call center agents for future fraudulent. Strong authentication and anti-fraud protections will be crucial here.
| The Racketeer Favorite Tactic: Man in the middle |
The Wolf Favorite Tactic: IVR Reconnaissance |
Mr. Roboto Favorite Tactic: ANI Spoofing |
Crash Override Favorite Tactic: Dark Web Data |
| The Good Samaritan Favorite Tactic: Social Engineering |
The Smurfette Favorite Tactic: IVR Reconnaissance |
Mr. Roboto Favorite Tactic: ANI Spoofing |
Explore more fraud profiles in our 2020 Voice Intelligence Report.
Where Do Attacks Begin in Contact Centers?
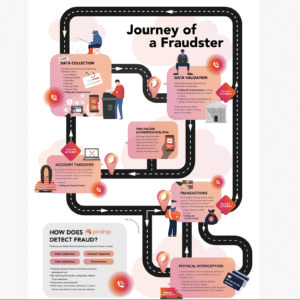

The Fraudster Toolkit:
Fraudsters use tools just like you do to help them optimize their performance. So we developed resources to help you build solid defenses. Below are the most popular tools fraudsters are using to cost you money, time, and customers – with links to show you how to stop it.
The Wire Cutters: Social Engineering
One of the core components of contact center fraud, but almost impossible to detect consistently without technology. Learn More – Webinar on demand
The Circular Saw: Voice Distortion
Many fraudsters alter their voice to bypass any voice biometric technology trying to create noise, or even as simple as using a higher or lower-pitched voice to more closely imitate their victim when talking to a contact center.
The Framing Hammer: Fraud Bible
As a possible legend or myth, the fraudster playbook known as the fraud bible read Pindrop’s position on the dark web trophy.
The Tape Measure: Data on Target Victim
Data reconnaissance and data dealing can mean big business for fraudsters, learn more about their techniques here, and how they supplement their own data with your IVR.
The Shovel: Account Mining
Fraudsters use a company’s own tools against them. Learn first hand how fraudsters use the IVR to verify stolen data and use automated dialers to dial account numbers and PINs.
The Handyman: Artificial Intelligence
AI is changing the world rapidly, including fraud. AI now has provided the ability to look and sounds like anyone else. If someone has a long youtube video of themself, that would be enough to replicate their voice and allow the fraudster to communicate as the victim to employees and contact center.
How to Detect Contact Center Fraud: Current Solutions for Contact Center Security
IVR Authentication As Fraud Prevention
It’s a bad idea. IVR authentication has it’s benefits, verifying supposedly genuine customers prior to the call’s connection to an agent. Pre-ring authentication lowers AHT, increases agent capacity, and improves CX but simple voiceprint to blacklist matching is not sufficient for fraud defense.
Real-Time Fraud Detection For Contact Centers
Real-time fraud detection used to be the gold standard of technological limits concerning anti-fraud solutions. However, fraudsters spend weeks attacking your IVR, validating data, honing processes, and even testing your fraud controls. The actual transaction and loss do not occur typically for another 30-60 days.
Graph Analysis for Fraud Detection in Contact Centers
Graph analysis has many applications. Capable of visualizing and analyzing extremely large data sets across any number of data points to reveal relationships between what seems to be unrelated activities. These relationships translate to patterns that may be indicative of fraudulent activity.
You can harness the power of your IVR in the form of predictive analytics. Learn more about preventing fraud in the IVR and learn how you can harness data from your phone channel to harden your entire contact center to attack.




