Articles
Deepfake Interviews: Sign of a Darker Future to Come?
Pindrop
author • 12th July 2022 (UPDATED ON 01/17/2025)
6 minute read time
The FBI has warned of an uptick in cases where “deepfakes” and stolen personal information are being used to apply for jobs in the U.S. — including faking video interviews. These headlines can captivate readers with wild stories about how these unusual occurrences are impacting an unfortunate few. If we look at recent history, should the trend of odd or amusing headlines that slowly evolve into near prevalent attack warnings with millions of dollars at stake give us concern?
1988 The Morris Worm – the first worm on the Internet.
Robert Morris created what we now consider the first worm on the internet. The potentially harmless exercise quickly became a vicious denial of service attack when a bug in the worm’s spreading mechanism leads to computers being infected and reinfected at a rate much faster than he anticipates. The worm did not damage or destroy files, but it still took its toll. The exact damages may not have been fully quantified, but estimates started at $100,000 and soared into the millions1.
The headline had a large impact on a nation just coming to grips with how important—and vulnerable—computers had become. The idea of cybersecurity became something computer users began to take more seriously. Just days after the attack, for example, the country’s first computer emergency response team was created in Pittsburgh at the direction of the Department of Defense. Developers also began creating much-needed computer intrusion detection software2.
The Morris Worm created a new generation of hackers and a wave of fraud minded attacks that still have implications on cybersecurity to this day.
1989 AIDS Trojan – the first ransomware attack
A physical disk purporting to be a database of AIDS information is mailed to thousands of AIDS researchers and subscribers to a UK computer magazine. It contains a Trojan (destructive program masquerading as a benign application) which impacted infected systems at a number of the prestigious colleges and public and private research centers that made up the early national electronic network3. To regain access, the users would have to send $189 to PC Cyborg Corporation at a PO box in Panama. The AIDS Trojan was pretty easy to overcome as it used simple symmetric cryptography and tools were soon available to decrypt the files4.
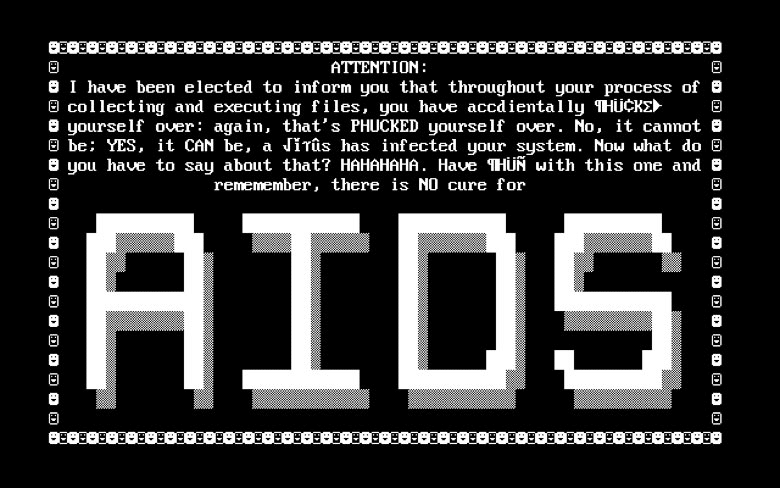
Ransomware has exploded since then, with the average ransom in 2024 costing $2.7 million – a rise of $1 million since 2023 according to Sophos.
1999 The Melissa Virus – attacking through attachments
In late March 1999, a programmer named David Lee Smith hijacked an America Online (AOL) account and used it to post a file on an Internet newsgroup named “alt.sex.” A virus would be unleashed on unsuspecting users thinking the attachment contained passwords for free access to adult websites.
The virus was not intended to steal money or information, but it wreaked plenty of havoc nonetheless. “Email servers at more than 300 corporations and government agencies worldwide became overloaded, and some had to be shut down entirely, including at Microsoft. Approximately one million email accounts were disrupted, and Internet traffic in some locations slowed to a crawl. Still, the collective damage was enormous: an estimated $80 million for the cleanup and repair of affected computer systems”5.
David Smith, the confessed author of the Melissa virus, pleaded guilty to computer crimes related to Melissa. He was released on bail and wasn’t sentenced for 29 months, receiving a 20 month sentence and $5,000 fine in 2002.
Melissa taught the world :
- how quickly computer viruses can rapidly increase.
- how difficult it is to trace the source of a virus
- how users can be exploited
- that there are no effective agency and government-wide processes for reporting and analyzing effects
- that computers can protect themselves from attacks when they are alerted to what is coming.
Like the Morris worm just over a decade earlier, the Melissa virus was a double-edged sword, leading to enhancements in online security while serving as an inspiration for a wave of even more costly and potent cyberattacks to come. For the FBI and its colleagues, the virus was a warning sign of a major germinating threat and of the need to quickly ramp up its cyber capabilities and partnerships.
Today, “deepfake” stories are charting similar path. Are we looking at the same beginning of the next cybersecurity nightmare at its infancy? Similarly to headlines of the day when the first worm was released, a lot of tongue in cheek and light approach from TV newscasts7 as a new and less understood threat in computers, the technology creating deepfakes could be taking the same path or all in fun, until the problem shows up closer to home.
2019 Deepfake Compromise- first national headlines of deepfake leading to loss
A high-profile case from 2019 offers a prime example. AI was used to mimic the voice of a German conglomerate’s CEO and trick an employee at another business into transferring funds to the wrong bank account. Cybercriminals managed to steal almost $250,000 from a U.K. based energy company with the scam. The victim said it sounded just like the CEO, even down to his slight accent.
March 2021 – first deep fake Red Herring?
A Pennsylvania mom who allegedly created deepfakes to frame her daughter’s cheerleading rivals.
However, an investigation from Cosmopolitan revealed that the racy videos of a teenage cheerleaders were in all likelihood completely real — and that the viral scandal that emerged from it was actually the result of incompetent police work. This could be a tipping point that sees deepfakes become mainstream enough people begin to blame the technology for incriminating audio or video of themselves. As this technology becomes harder to spot, how will that impact how we view any content in terms of authenticity?
July 2022 FBI Warns Against Deepfake Interviewees
A genuine uptick in cases where “deepfakes” and stolen personal information are being used to apply for jobs in the U.S so much that the FBI posts a notice. An article featured by Techcrunch starts off by saying, “A lot of people are worried about the prospect of competing with AI for their jobs, but this probably isn’t what they were expecting.” A eelierly familiar ‘serious but light’ tone of what the problem is being reported in the news, just like early cyber threats, despite coming from the FBI. How long before these warnings are so numerous and we ourselves get “deepfaked” so much (like getting a vishing email or spam call today) that we are so numb that the headlines no longer garner a smile, but disconcert for how we got here.
The only way to protect is through vigilant education. Start by reading our Voice Intelligence Report to see what threats should not be ignored.
1https://www.fbi.gov/history/famous-cases/morris-worm
2https://www.fbi.gov/history/famous-cases/morris-worm
3https://www.sdxcentral.com/security/definitions/what-is-ransomware/case-study-aids-trojan-ransomware/
4https://www.knowbe4.com/aids-trojan
5https://www.insidehook.com/article/history/melissa-virus-changed-internet
6https://www.insidehook.com/article/history/melissa-virus-changed-internet
7https://www.youtube.com/watch?v=fj8S6Hd-5bk&ab_channel=Kahvowa




