Articles
Three Top Types of Fraud + What to Do When It Happens
3 minute read time
Every year since 2003, October has been recognized as Cyber Security Awareness Month (CSAM). In honor of this year’s CSAM, we wanted to cover the three top fraud types and what you can do when they happen. Fraud can occur when you least expect it and is changing so quickly that it’s essential to stay current and continue to evolve your protection and prevention strategy. This trend is anticipated to continue, especially when fraud was up 40% this past year.
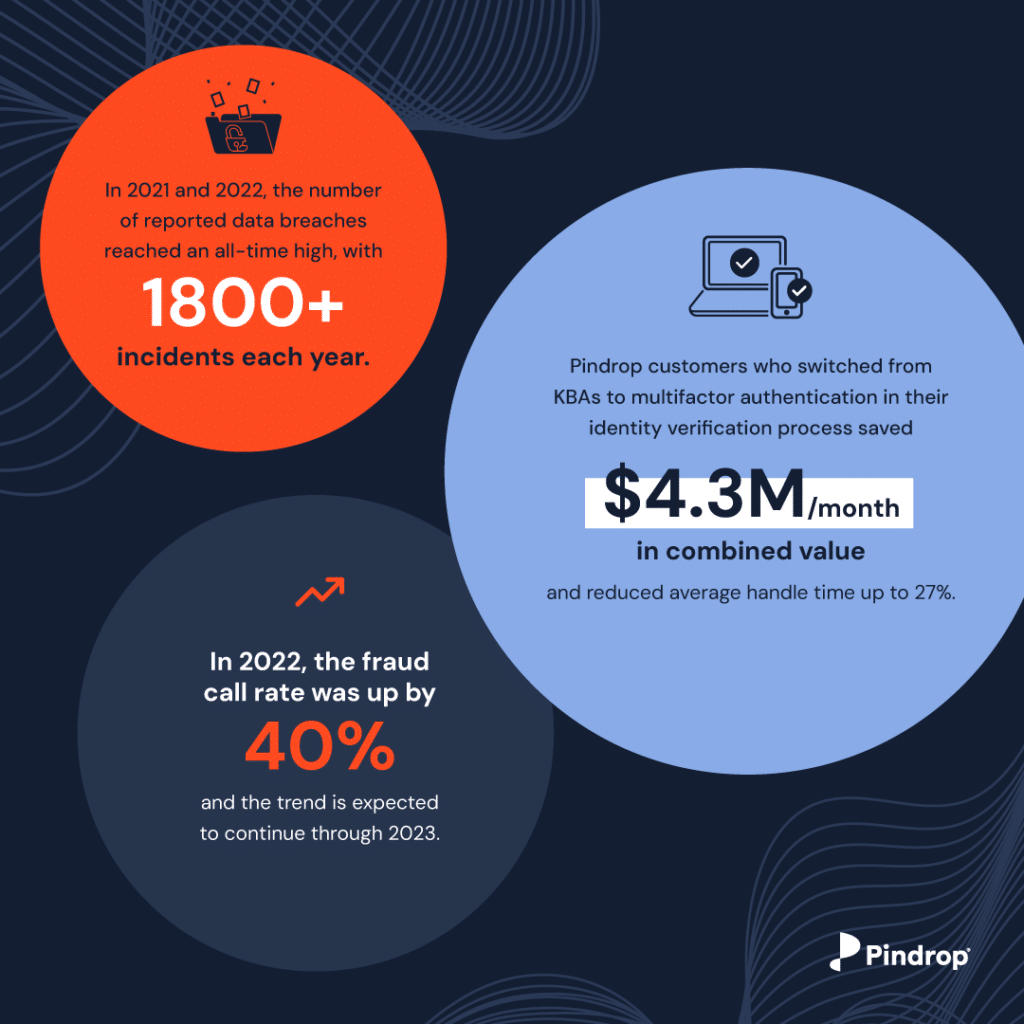
So what are the top fraud types, and how can you safeguard your business and customers if and when they happen? New data shows that the Federal Trade Commission received 2.8 million fraud reports from consumers in 2021, a 70% increase over the previous year, leading to more than $5.8 million in losses. The most commonly reported category once again was the imposter scam, where a fraudster represents themself as someone else to extract money or personal information from a victim. But fraud attacks can also be carried out by someone affiliated with the victim. Here are the top three instances of fraud defined:
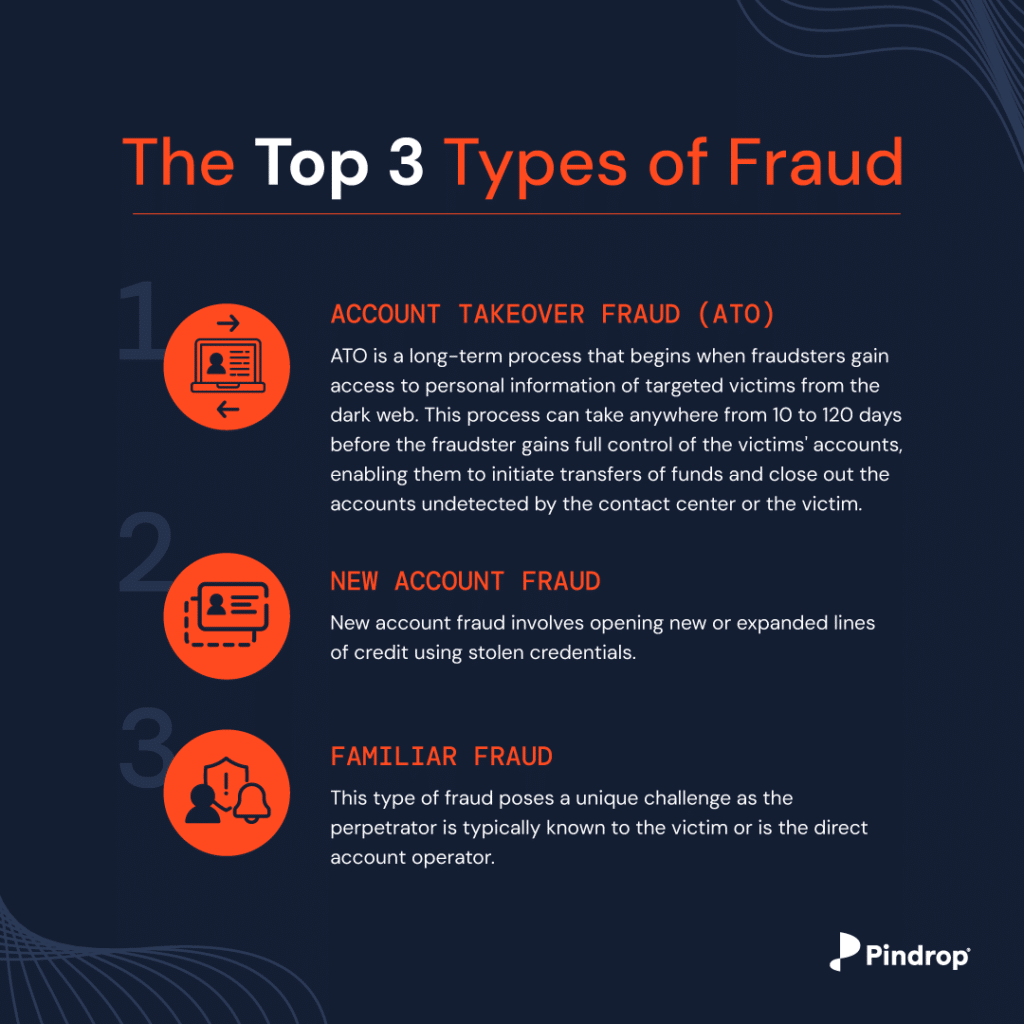

When these common types of fraud occur, there are a few steps you can take to quickly mitigate damaging results to your brand, security posture, and operations. For instance, Pindrop’s anti-fraud voice detection stopped $146 million in fraudulent transactions for PSCU, a credit union company. Here are the steps you can apply to your business to detect and protect against fraud.
Step 1 – Bet on the cloud
Having APIs built for flexible access allows security systems to work in your favor. The cloud can then work to authenticate callers and obtain fraud behavior feedback for faster detection.
Step 2 – Have Multiple Authentication and Risk Signals
Implementing a multifactor authentication within your contact center allows you to offer faster, more secure, and personalized customer service. Include it within your system or process so that it is utilized within a device, behavior, voice, risk, and network for one seamless flow. This allows for secure and simple self-service options for agents and customers to handle real-time authentication.
Step 3 – Empower your Fraud Detection Process with Custom Attributes
Custom attributes utilize data tags to enhance data integration between call center systems and solutions with customizable details. Analysts can conduct more impactful and thorough fraud investigations by enabling custom tags.
Step 4 – Leverage the Collaboration of Authentication and Detection Processes
Ensure you leverage a platform for effective identity management for users, roles, and permissions to support transparent and accessible collaboration, especially for customer-facing applications. Consulting services should also be available to catch real-time fraud and maintain organizational efficiency. Lastly, it’s important to include developer resources such as API specifications.







